Cryptohorrific – Hack The Box¶
Difficult: Medium
Category: Mobile
OS: iOS
Description: Secure coding is the keystone of the application security!
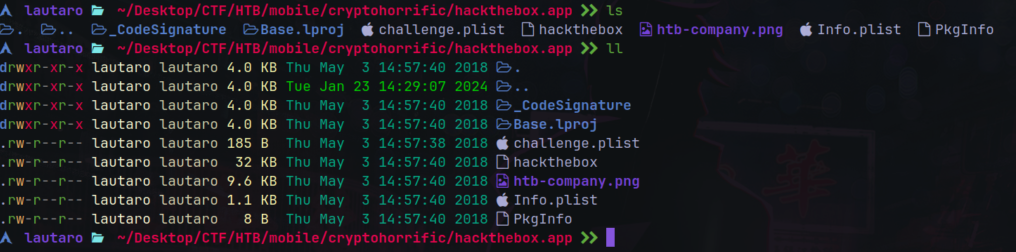
After downloading the compressed file and decompressing it, we will have a folder where inside we find the files we need:
The hackthebox file, is the main file of the program that contains the binary files.
The .plist file is a list that contains details about the app and author.
This is for gather information when you search an App in the App Store.
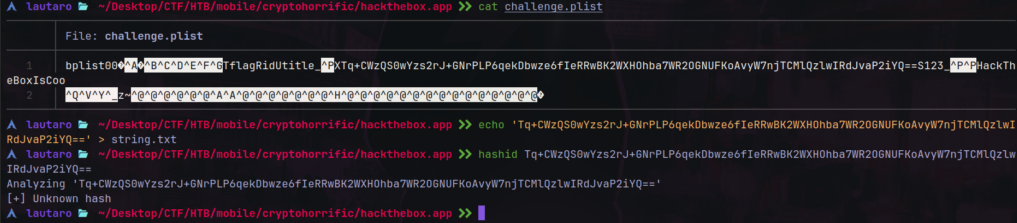
The challenge.plist have some interesting:
This must be an base64 encrypted text.
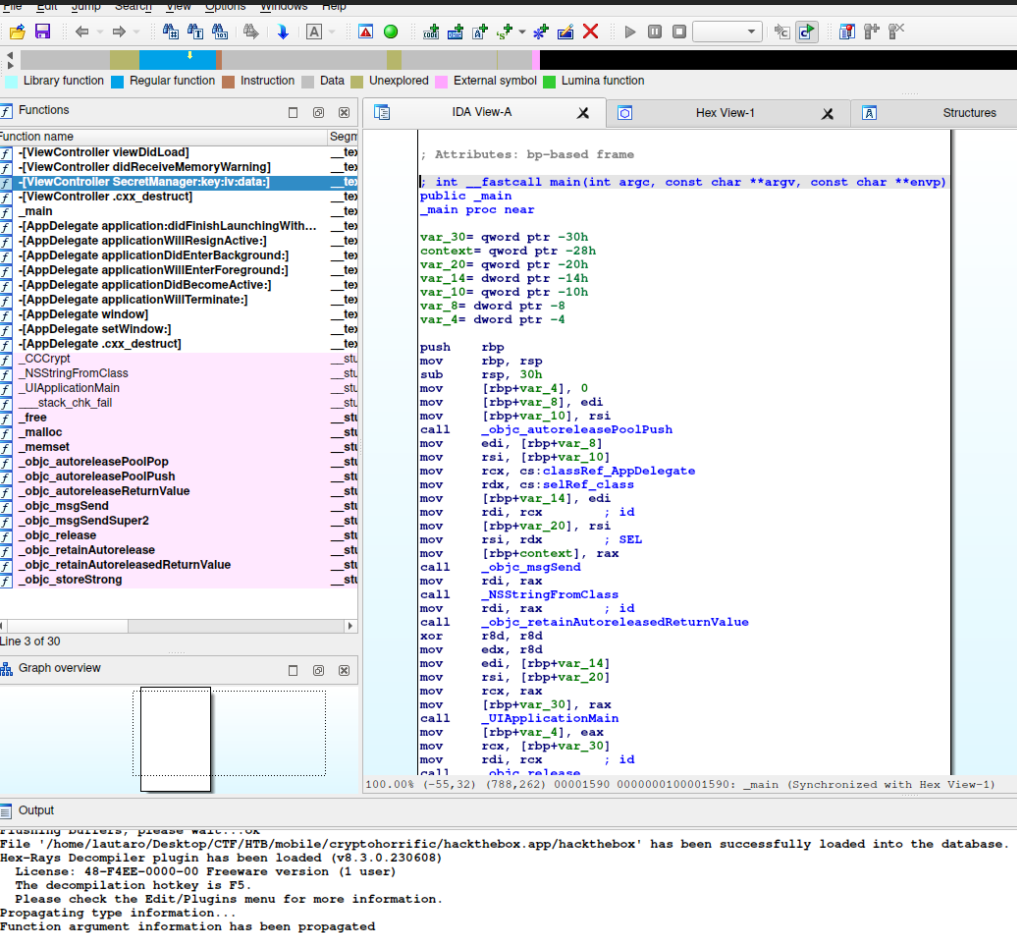
So it’s source code time.I recommend use IDA for that:
We load the hackthebox program to our IDA and let’s inspect that.
Here we have a insteresting function: _CCCrypt
Following to CCCrypt_ptr we can see that jmp. So, navigate to CCCrypt_ptr and:
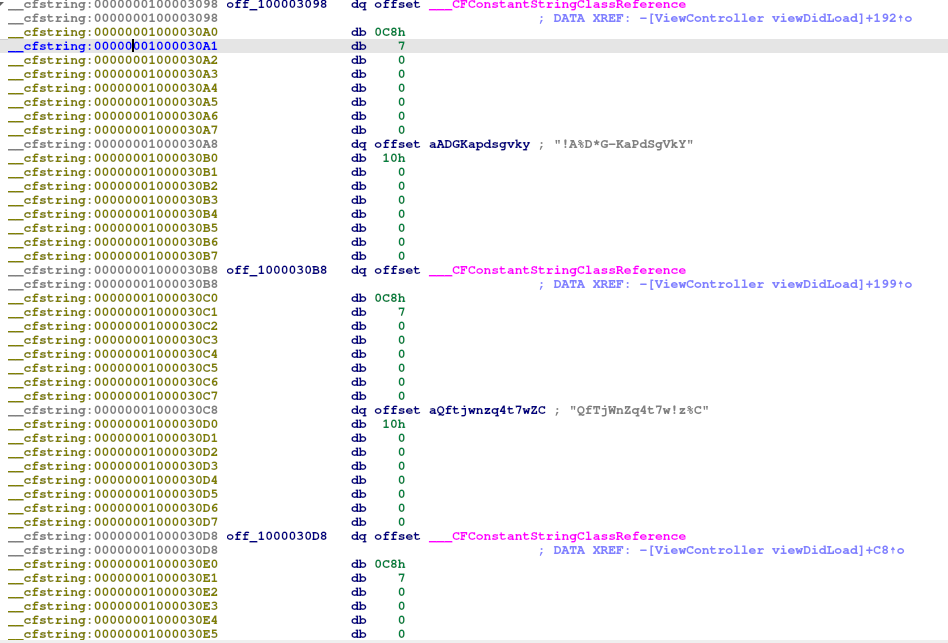
We can see between __cfstring some interesting things:
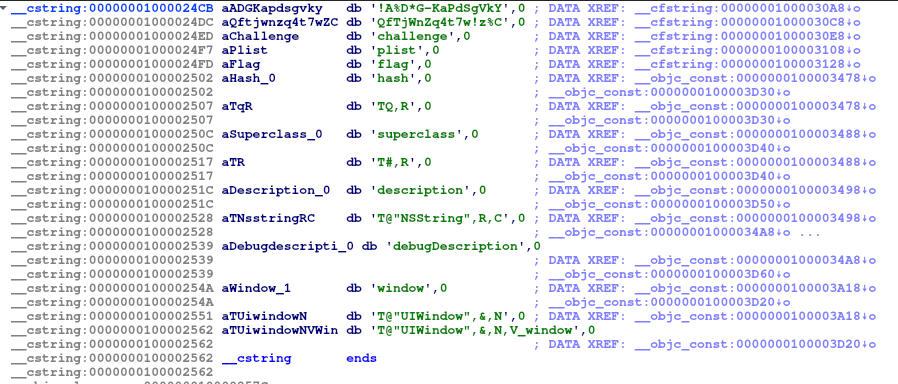
Following, for example: aADGKapdsgvky
We are redirect to:
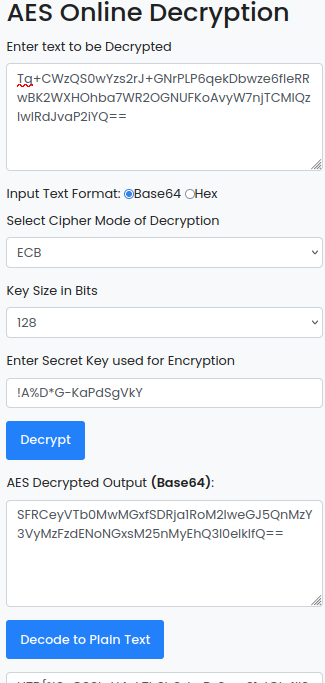
And may be this is the key and IV of an AES encryption. Let’s check:
So with these values, we can go to this online tool for decrypt:https://www.devglan.com/online-tools/aes-encryption-decryption
And here is, the flag:
Decode to Plain Text and you will get the flag.
I hope you found it useful (: